Thanks for the reply,
The video was stalling too much so i had to bail before you got to that part, the chaos-shorts element… i’ve already discarded the guy on the right of your image… the guy with the badge was not my #2 clone… Badge-guy is not wearing a shirt that would look grey at a distance… The other one in grey was at the west side of the fence-crowd, but i’ve only seen a part of that person in an image…
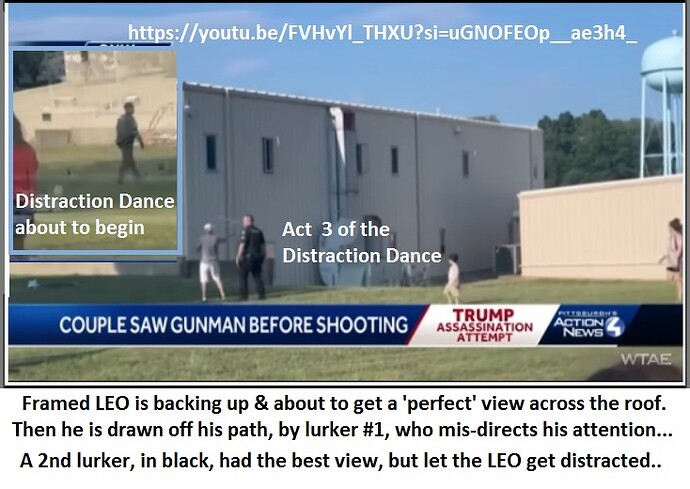
A detail that you covered in your short glance over this angle, is the placement of the LEO who walked away from white socks/cap guy…
The intereaction that occurred before that is where the guy on the gunman’s 6, BC/WS-guy, bought the shooter a few seconds more…
What i find so bizzar is that two guys remained in the line of fire that could have come from the LEO who you pointed out under the tree… Why didn’t he stand on the wall, as you’ve said, but also why wasn’t an assault made from the west side, a fully protectedable vector…
The LEO’s were caught up in some layer of confusion and that confusion could have been manufactured by our two look-alikes, who would have lowered the sense of concern by being visible in the area of concern… That one of them held a back door position, and also waltzed an LEO off the line of sight, cannot be left unexamined…
If you’re off on a tangent of top-down examination, especially with the eastside distraction of released BC-footage, and have not asked where is the west side footage, then you’ve missied the simple means of putting pressure on the stone-wallers in government…
Plausible exusibility does them a favor so count on it being a part of an inside job involving very few officials and a few willing bottom-feeder assets…
Assuming that anti-trump element were not involved is illogical… Have we not learned from J6th?? And surprise, they’ve back off from geo-fencing… Great timing…
If reasonable evidence can be established that this was a team effort, not a loner on a mission, that opens up a vista for factors which then need to be handled by the official narrative, such as all the time the patsey spent around an LEO training facility, and the sharp shooter competition that just so happened to be in town that week…
Watch carefully the interaction between ball-cap/socks guy and ask:
Did he really know where the gunman was, or was he just acting that way to draw attention and insert misdirection, if needed…
His mannerisms are too theatrical to be overlooked…
Sorry to say i had to image-skip to one spot where you covered this factor, i couldn’t listen to all of your talk, partly because of buffering interuptions ,but also because i don’t want to emerse my mind in the confusion that others express…
Red flags went off in me when i saw this guy sitting were he was during the initial west-side commotion, and those flags have not decreased…
And now i’m locked out of my X account where this was all being layed out and sent to Congressional members taking an interest an investigation… Restriction timing is Very strange…
…